BOOK THIS SPACE FOR AD
ARTICLE AD
Startups have begun to disclose data breaches after a massive leak of stolen databases was published on a hacker forum this month.
This week, BleepingComputer was the first to report that ShinyHunters, a threat actor known for data breaches, began to leak the stolen databases of eighteen web sites for free on a hacker forum.
Most of the companies targeted by these attacks appear to be startups, with the full list of the 18 data breaches and their updated disclosure status are listed below:
| Company | User Records | Reported Breach Date | Known? |
| Appen.com | 5.8 Million | N/A | No |
| Chatbooks.com | 15.8 Million | March 26th, 2020 | Yes |
| Dave.com | 7 Million | July 2020 * | Yes |
| Drizly.com | 2.4 Million | July 2020 * | Yes |
| GGumim.co.kr | 2.3 Million | March 2020 * | Yes |
| Havenly.com | 1.3 Million | June 2020 * | No |
| Hurb.com | 20 Million | N/A | Yes |
| Indabamusic.com | 475 Thousand | N/A | No |
| Ivoy.mx | 127 Thousand | N/A | No |
| Mathway.com | 25.8 Million | January 2020 * | Yes |
| Proctoru.com | 444 Thousand | N/A | No |
| Promo.com | 22 Million | July 2020 | Yes |
| Rewards1.com | 3 Million | July 2020 * | No |
| Scentbird.com | 5.8 Million | N/A | Yes |
| Swvl.com | 4 Million | N/A | Yes |
| TrueFire.com | 602 Thousand | N/A | Yes |
| Vakinha.com.br | 4.8 Million | N/A | No |
| Wattpad | 270 Million | June 2020 * | Yes |
| * Based on threat actor's statements | |||
ShinyHunters told BleepingComputer that they released the databases for free to benefit the "community" and as they already made enough money from selling them in private sales.
Days after contacting these companies about the breaches, data breach disclosures have started to trickle in, with Drizly and Scentbird being the first ones.
Drizly discloses data breach
On July 27th, BleepingComputer contacted alcohol delivery startup Drizly regarding a database containing approximately 2.5 million records leaked for free on a hacker forum.
This database, whose table is shown below, contained user's email, names, hashed passwords, addresses, phone numbers, and other information.
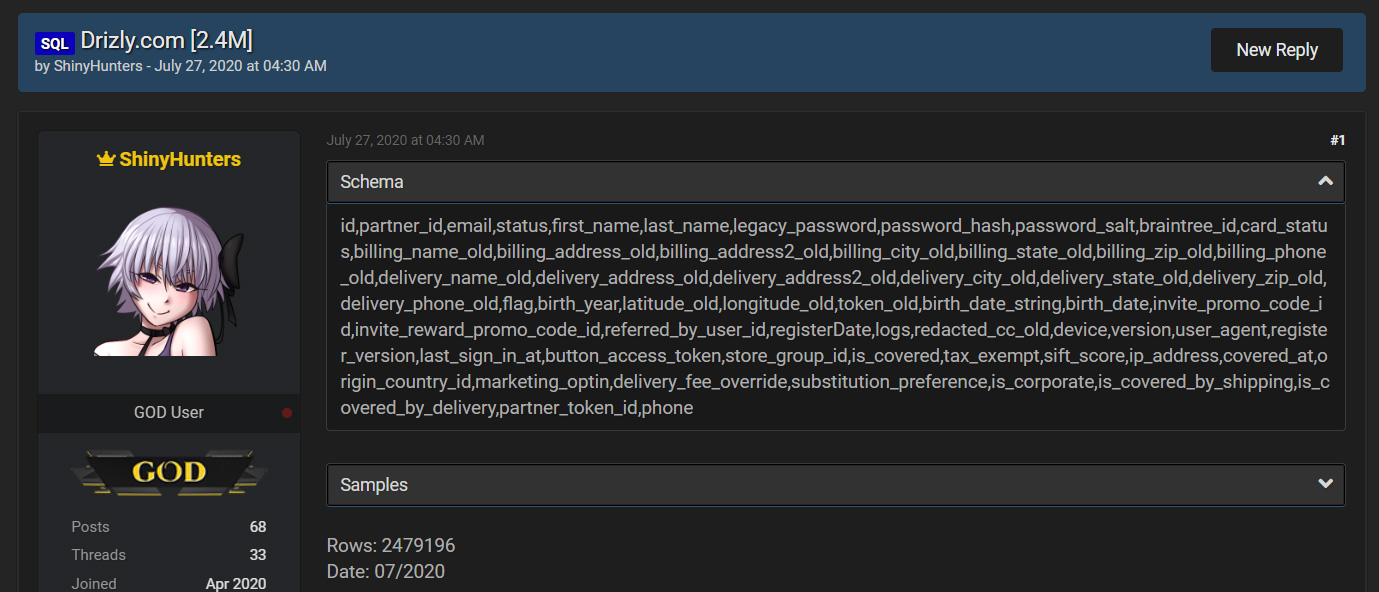 Drizly database leak
Drizly database leakA day after reporting the leak, Drizly told BleepingComputer that the breach was detected on July 13th, when an investigation was started.
"Drizly first identified that some customer data may have been impacted on July 13th and immediately began a forensic investigation with cyber security experts to understand what had happened and what information was impermissibly obtained. In addition, we quickly took steps to tighten security and further reduce risk of attack.
In terms of scale, up to 2.5 million accounts have been affected. Delivery address was included in under 2% of the records. And as mentioned in our email to affected consumers, no financial information was compromised. Hashed passwords were taken, though we use BCrypt, an industry favored hashing algorithm, to encrypt the passwords. Because of the encryption Drizly accounts should not be able to be accessed, though to be cautious we’ve encouraged users to nonetheless change their passwords."
From their statement, Drizly does not appear to be requiring users to reset their passwords.
As the exposed hashed passwords can potentially be decrypted, all Drizly users should immediately change their password at the site and at any other site that utilizes the same password.
Scentbird disclosed data breach soon after
BleepingComputer also contacted fragrance subscription service Scentbird after their database was leaked for free by ShinyHunters.
This database contains users' email, name, hashed password, birthday, gender, whether they are influencers, and other customer information.
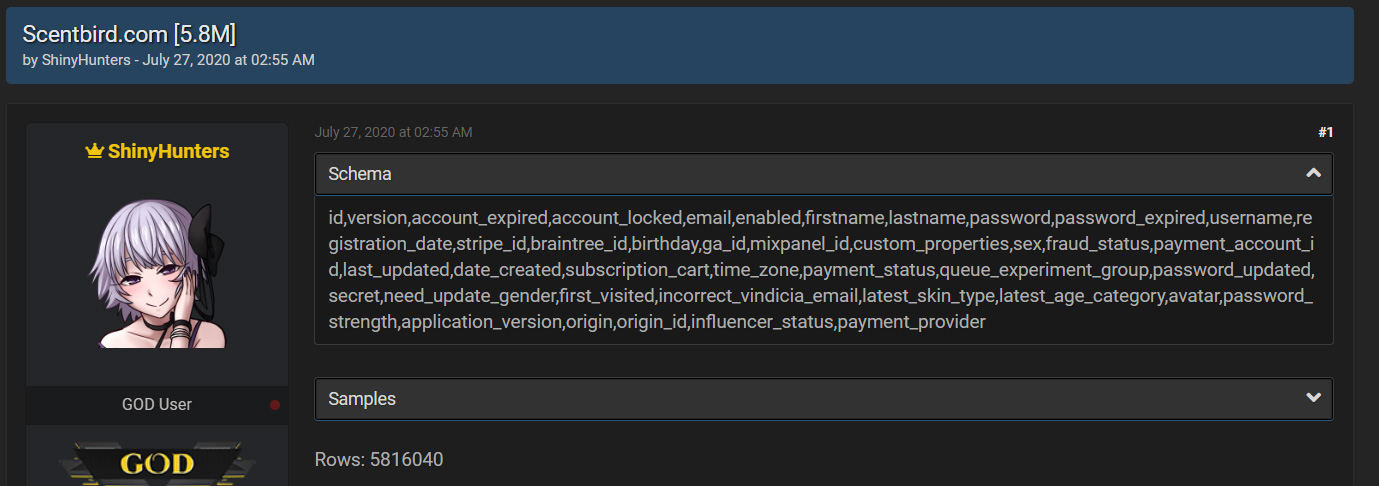 Scentbird database leak
Scentbird database leakBleepingComputer did not receive a response to our inquiry, but in a notification seen by BleepingComputer, Scentbird has disclosed the data breach.
"We are writing to let you know that Scentbird recently learned that unauthorized individuals may have accessed a database containing the personal information of Scentbird’s users. We launched an investigation as soon as we became aware of this incident, and our investigation is in its initial stages. We wanted to notify you right away, however, so that you can take action to protect yourself."
"We have no reason to believe that the incident affected social security numbers, government-issued ID numbers, or full credit or debit card numbers. We do not maintain this type of information about users. Depending on the type of account you maintained, the affected information may have included your name, email address, encrypted Scentbird account password, billing and shipping address, date of birth (if you chose to provide this information), and gender," Scentbird disclosed.
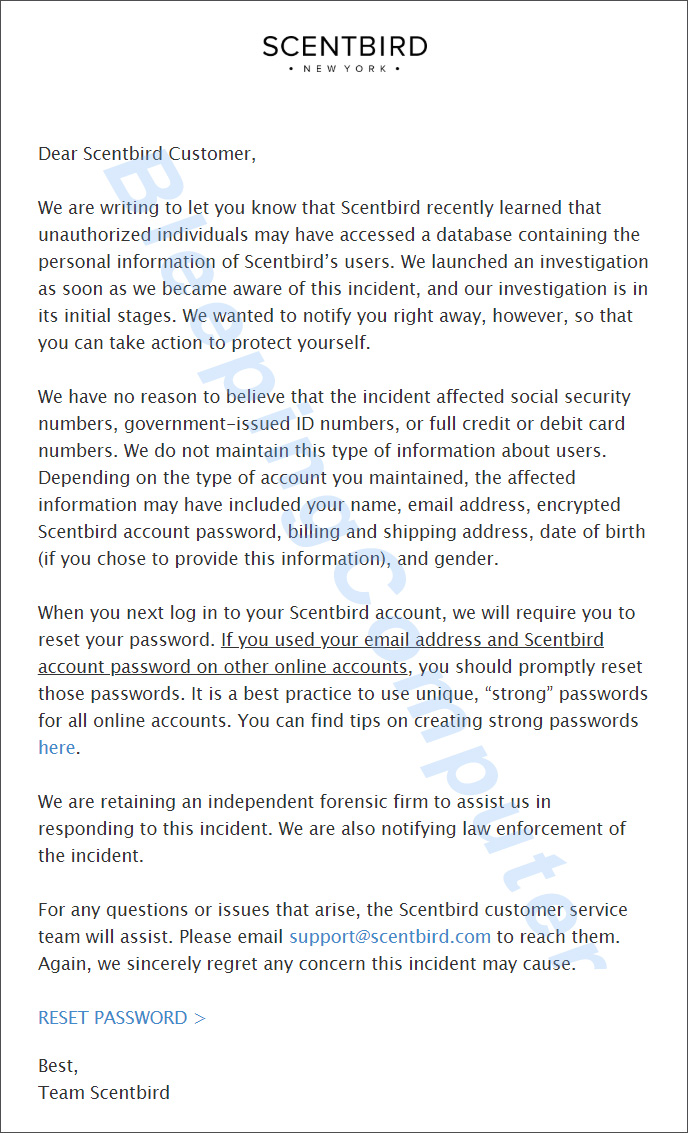 Scentbird notification
Scentbird notificationScentbird states that they are performing a mandatory password reset for all users when they next log into the site.
Like Drizly, if your Scentbird password is used at other sites, you should immediately change the password at these sites so that your accounts are not breached.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·