BOOK THIS SPACE FOR AD
ARTICLE AD
Ransomware gangs continue to attack schools, companies, and even hospitals worldwide with little sign of letting up. Below we have tracked some of the ransomware stories that we are following this week.
Stories of particular interest revolve around new features and tactics used by some of the ransomware operations.
After analyzing the Conti training material leaked earlier this month, we learned that they use a legitimate remote access software to retain persistence on a compromised network. We also learned that they prioritize searching for cyber insurance policies and financial documents after taking control of a network.
Another report illustrates how threat actors are tracking researchers on Twitter as a new ransomware gang known as LockFile uses the PetitPotam attack to take over Windows domains.
Some of the attacks we saw this week were against the Brazilian National Treasury, Memorial Health System, and Japanese insurer Tokio Marine.
Finally, there is some good news, as Emsisoft has released a SynAck ransomware decryptor after the master decryption keys were released by the threat actors earlier this month.
Contributors and those who provided new ransomware information and stories this week include: @malwareforme, @DanielGallagher, @jorntvdw, @Seifreed, @Ionut_Ilascu, @struppigel, @PolarToffee, @demonslay335, @VK_Intel, @BleepinComputer, @serghei, @malwrhunterteam, @FourOctets, @fwosar, @LawrenceAbrams, @symantec, @emsisoft, @AdvIntel, @IBMSecurity, and @fbgwls245.
August 14th 2021
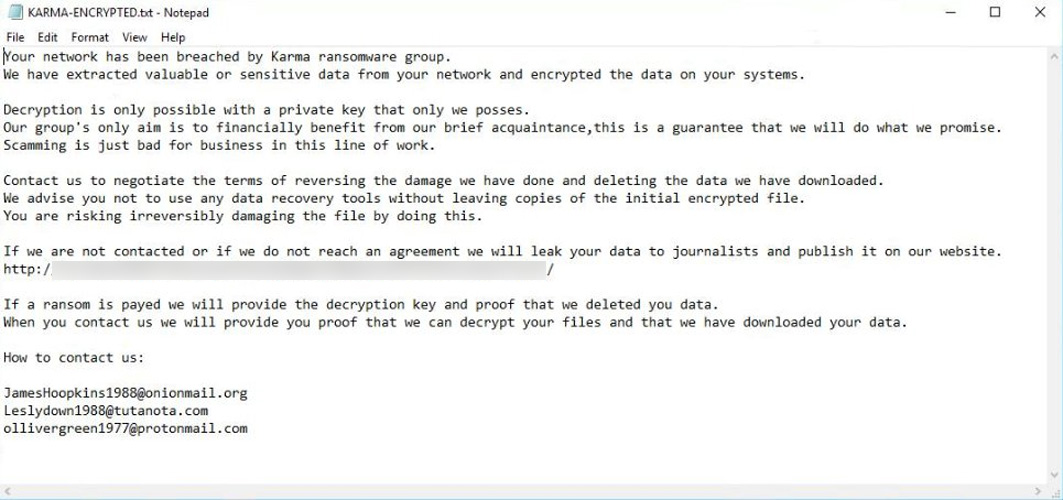
New Karma ransomware
dnwls0719 found a a new Karma ransomware that appends the .KARMA extension and has a dedicated leak site.
August 16th 2021
Hive ransomware attacks Memorial Health System, steals patient data
In what appears to be an attack from the Hive ransomware gang, computers of the non-profit Memorial Health System have been encrypted, forcing staff to work with paper charts.
Colonial Pipeline reports data breach after May ransomware attack
Colonial Pipeline, the largest fuel pipeline in the United States, is sending notification letters to individuals affected by the data breach resulting from the DarkSide ransomware attack that hit its network in May.
August 17th 2021
Conti ransomware prioritizes revenue and cyberinsurance data theft
Training material used by Conti ransomware affiliates was leaked online this month, allowing an inside look at how attackers abuse legitimate software and seek out cyber insurance policies.
Brazilian government discloses National Treasury ransomware attack
The Brazilian Ministry of Economy has disclosed a ransomware attack that hit some of National Treasury's computing systems on Friday night, right before the start of the weekend.
New Dharma ransomware variant
Jakub Kroustek found a new Dharma variant that appends the .c0v extension.
August 18th 2021
Diavol ransomware sample shows stronger connection to TrickBot gang
A new analysis of a Diavol ransomware sample shows a more clear connection with the gang behind the TrickBot botnet and the evolution of the malware.
Japanese insurer Tokio Marine discloses ransomware attack
Tokio Marine Holdings, a multinational insurance holding company in Japan, announced this week that its Singapore branch, Tokio Marine Insurance Singapore (TMiS), suffered a ransomware attack.
August 19th 2021
CISA shares guidance on how to prevent ransomware data breaches
The US Cybersecurity and Infrastructure Security Agency (CISA) has released guidance to help government and private sector organizations prevent data breaches resulting from ransomware double extortion schemes.
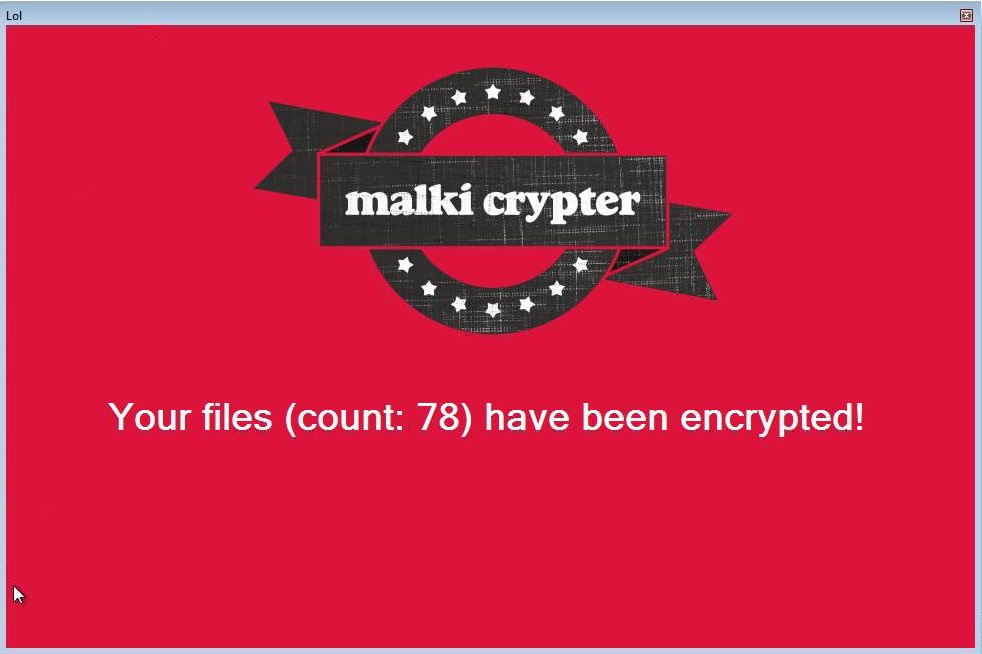
New Malki Ransomware
dnwls0719 found a new ransomware that appends the .MALKI extension.
August 20th 2021
SynAck ransomware decryptor lets victims recover files for free
Emsisoft has released a decryptor for the SynAck Ransomware, allowing victims to decrypt their encrypted files for free.
LockFile ransomware uses PetitPotam attack to hijack Windows domains
At least one ransomware threat actor has started to leverage the recently discovered PetitPotam NTLM relay attack method to take over the Windows domain on various networks worldwide.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·