




Token-related functionality
Obtaining tokens
Open process/thread token Open effective thread token (via direct impersonation) Query session token Log in user using explicit credentials Log in user without
credentials (S4U logon) Duplicate tokens Duplicate handles Open linked token Filter tokens Create LowBox tokens Created restricted tokens using Safer API Search for opened handles Create anonymous token Impersonate logon session token via pipes Open clipboard token
Highly privileged operations
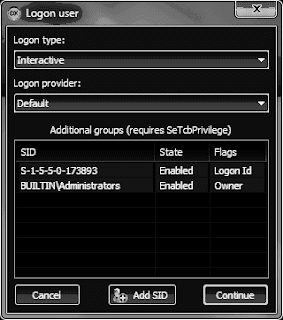
Add custom group membership while logging in users (requires
Tcb Privilege) Create custom token from scratch (requires
Create Token Privilege)
Viewing
User Statistics, source, flags Extended flags (TOKEN_*) Restricting SIDs App container SID and number Capabilities Claims Trust level Logon session type (filtered/elevated/default) Logon session information Verbose terminal session information Object and handle information (access, attributes, references) Object creator (PID) List of processes that have handles to this object Creation and last
modification times
Viewing & editing
Groups (enable/disable) Privileges (enable/disable/remove) Session Integrity level (lower/raise) UIAccess, mandatory policy
Virtualization (enable/disable & allow/disallow) Owner and primary group Originating logon session Default DACL Security descriptor Audit overrides Handle flags (inherit, protect)
Using
Impersonation Safe impersonation Direct impersonation Assign primary token Send handle to process Create process with token Share with another instance of TokenUniverse
Other actions
Compare tokens Linking logon sessions to create UAC-friendly tokens Logon session relation map
AppContainer profiles
Viewing AppContainer information Listing AppContainer profiles per user Listing child AppContainers Creating/deleting AppContainers
Local Security Authority
Global audit settings Per-user audit settings Privilege assignment Logon rights assignment Quotas Security Enumerate accounts with privilege Enumerate accounts with right
Security Account Manager
Domain information Group information Alias information User information Enumerate domain groups/aliases/users Enumerate group members Enumerate alias members Manage group members Manage alias members Create groups Create aliases Create users Sam object tree Security
Process creation
Methods
CreateProcessAsUser CreateProcessWithToken WMI RtlCreateUserProcess RtlCreateUserProcessEx NtCreateUserProcess NtCreateProcessEx CreateProcessWithLogon (credentials) ShellExecuteEx (no token) ShellExecute via IShellDispatch2 (no token) CreateProcess via code injection (no token) WdcRunTaskAsInteractiveUser (no token)
Parameters
Current directory Desktop Window show mode Flags (inherit handles, create suspended, breakaway from job, ...) Environmental variables Parent process override Mitigation policies Child process policy Job assignment Run as invoker compatibility AppContainer SID Capabilities
Interface features
Immediate crash notification Window station and desktop access checks Debug messages reports
Process list
Hierarchy Icons Listing processes from Low integrity & AppContainer Basic actions (resume/suspend, ...)
Customizable columns Highlighting Security Handle table manipulation
Interface features
Restart as SYSTEM Restart as SYSTEM+ (with
Create Token Privilege) Customizable columns Graphical hash icons Auto-detect inherited handles Our own security editor with arbitrary SIDs and mandatory label modification Customizable list of suggested SIDs Detailed error status information Detailed suggestions on errors
Misc. ideas
[?] Logon session creation (requires an
authentication package?) [?] Job-based token filtration (unsupported on Vista+) [?] Privilege and audit category description from wsecedit.dll
.png)
 2 years ago
183
2 years ago
183 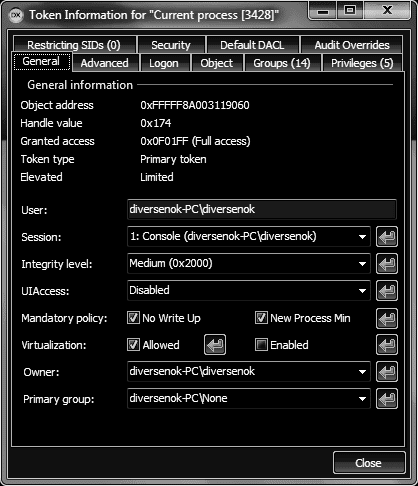






















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·