BOOK THIS SPACE FOR AD
ARTICLE AD
Employees of U.S. defense and aerospace contractors were targeted in a large scale spear-phishing campaign between early April and mid-June 2020 in a series of phishing attacks designed to infect their devices and to exfiltrate defense tech intelligence.
Throughout this series of attacks dubbed 'Operation North Star' by McAfee Advanced Threat Research (ATR) researchers who spotted it, the spear-phishing emails were camouflaged as fake job offers from high-profile defense contractors, a tactic used by other similar campaigns targeting the same industries in 2017 and 2019.
McAfee linked these attacks to the Hidden Cobra, the threat group behind the previous military cyber-espionage phishing campaigns, based on similarities found in implant execution code and core functionality.
Hidden Cobra is an umbrella term used by the US Intelligence Community to track North Korean malicious cyber activity attributed to several hacking groups including but not limited to APT 37, Lazarus Group, APT 38, DarkHotel, Kimsuky, and Andariel.
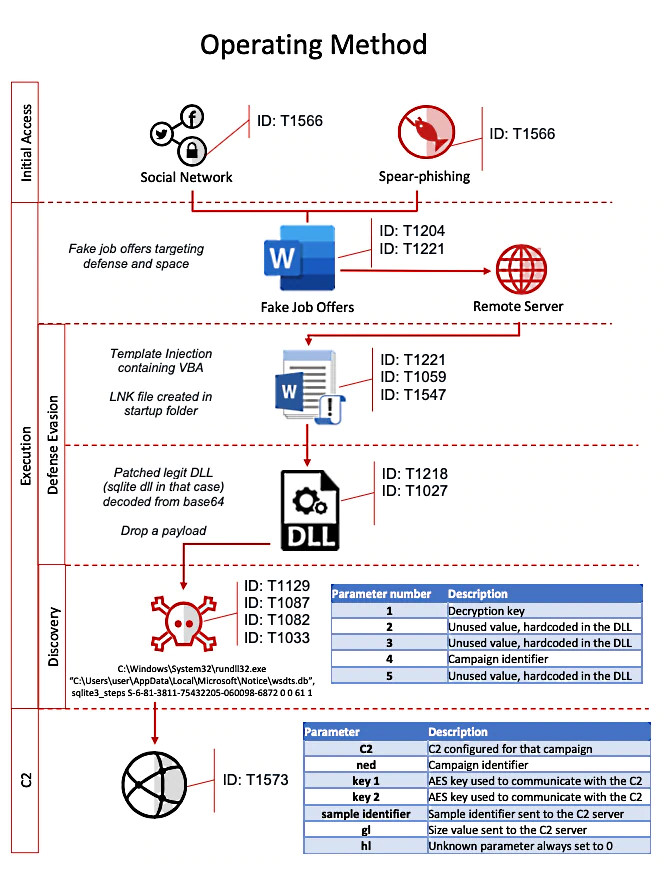 Operation North Star attack flow (McAfee)
Operation North Star attack flow (McAfee)Cyber-espionage campaign targeting defense intelligence
The main goal of this campaign was to collect military and defense tech intelligence from experienced aerospace and defense employees, later to be exfiltrated to compromised infrastructure from European countries also used to deliver malicious implants to targets' infected devices.
"The lure documents contained job descriptions for engineering and project management positions in relationship to active defense contracts," McAfee said.
"The individuals receiving these documents in a targeted spear phishing campaign were likely to have an interest in the content within these lure documents, as we have observed in previous campaigns, as well as some knowledge or relationship to the defense industry."
The fake job offerings were sent by attackers posing as "recruiters" to potential victims through both phishing emails and social networks.
They included Senior Design Engineer and System Engineer positions at US defense programs and groups such as the F-22 Fighter Jet Program, Defense, Space and Security (DSS) jobs, the Aeronautics Integrated Fighter Group, and multiple military aircraft modernization programs.
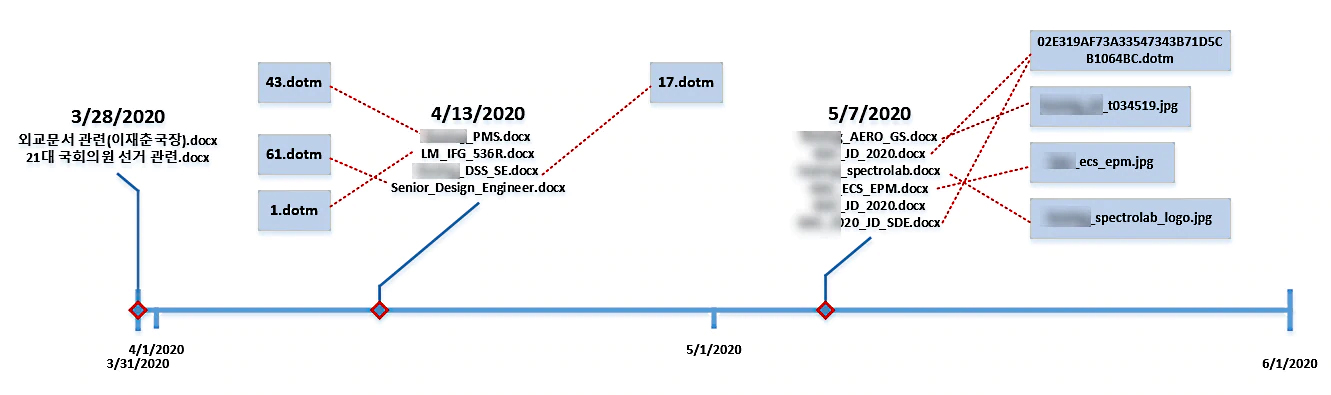 Phishing document creation timeline (McAfee)
Phishing document creation timeline (McAfee)North Korean malicious activity
This operation lines up with similar North Korean intelligence gathering and financially motivated efforts recently reported by security researchers with private cyber-security firms and government organizations.
Since April 2020, the U.S. government is offering a reward of up to $5 million for any info on any DPRK hackers' cyber activity, including past or ongoing campaigns if that leads to the disruption of illegal activities or the identification of North Korean actors involved.
In March 2020, two Chinese nationals were charged for laundering over $100 million worth of cryptocurrency out of roughly $250 million stolen by Lazarus North Korean hackers in 2018 as part of a single cryptocurrency exchange hack.
In all, United Nations (UN) Security Council experts say that North Koreans were behind cryptocurrency heists that led to financial losses of $571 million in 2017 and 2018, with the U.S. Treasury having sanctioned three DPRK-sponsored hacking groups (Lazarus, Andariel, and Bluenoroff) in September 2019.
In more recent news, North Korean hackers have also been linked by web security company Sansec to credit card stealing attacks targeting the online stores of large US and European retailers for at least a year.
Kaspersky researchers also discovered that Lazarus Group hackers have developed and are actively using VHD ransomware against enterprise targets and are also stealing data using a recently spotted malware framework known as MATA.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·