BOOK THIS SPACE FOR AD
ARTICLE AD
IDOR — Insecure Direct Object Reference, abuse of the lack of authentication at every stage.
A while ago, I curled up in bed, with my laptop and a coffee, and scraped every single IDOR report from hackerone. A week or so later, I had compiled notes and findings from my reading and I’m here to show you what I’ve learnt, and how my understanding of a seemingly simple bug has changed massivley.
For reference, throughout the article I will refer to various bug reports via numbers, these numbers correlate to bug reports, which can be found by replacing XXXXXX in the url: https://hackerone.com/reports/XXXXXX
That subheading was pretty dramatic, realisitcally, it should be “Your understanding of IDOR is too narrow”. Typically people think an IDOR is just finding a parameter called “ID” (or similar) and replacing the number with another, like report 797685.
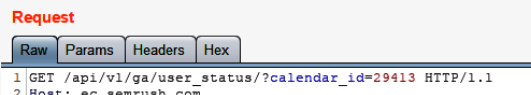
Then receiving Status 200, saying an operation from a different user has been complete.
![]()
IDOR is wider than this. IDOR does not have to apply to accounts. It doesnt not have to apply to IDs. It is not just found in basic formats. We will discuss this misunderstanding in a bit more detail.
When reading these reports, I counted where I found the various weakness emerged and here are the results:
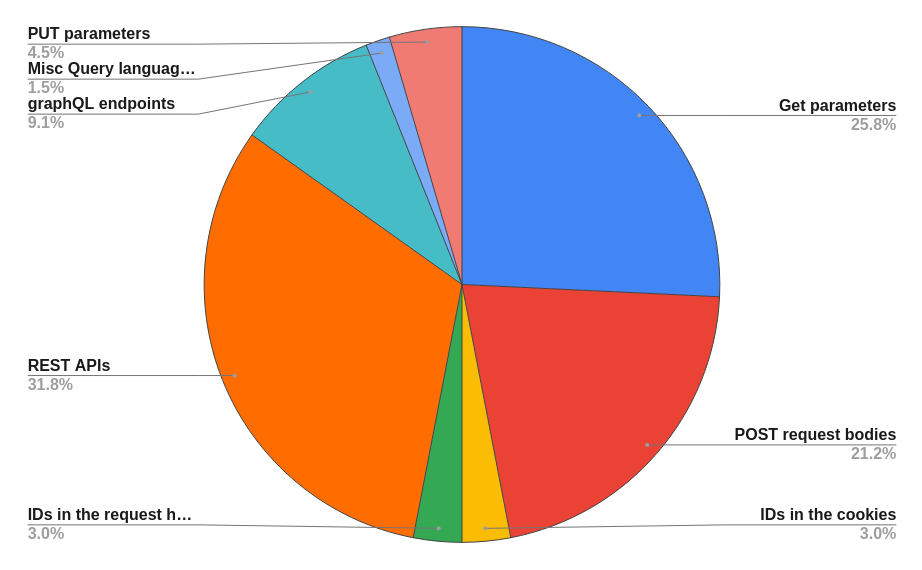
This is often an idea which I hear propagated; it is a fairly reductionist way of thinking about this bug. Although it may be more technically simple than most other bugs, there are still concepts you can learn to increase your success with them. And it is still the bug which yeilds higher bounties, than Privesc, SQLi and Code Injection.
Here are some points to keep in mind:
Can you find IDs that arent incremental? Sometimes an ID can be found by visiting a page or an asset.![]()
An ID can be found in the source code on a page in a twitter:

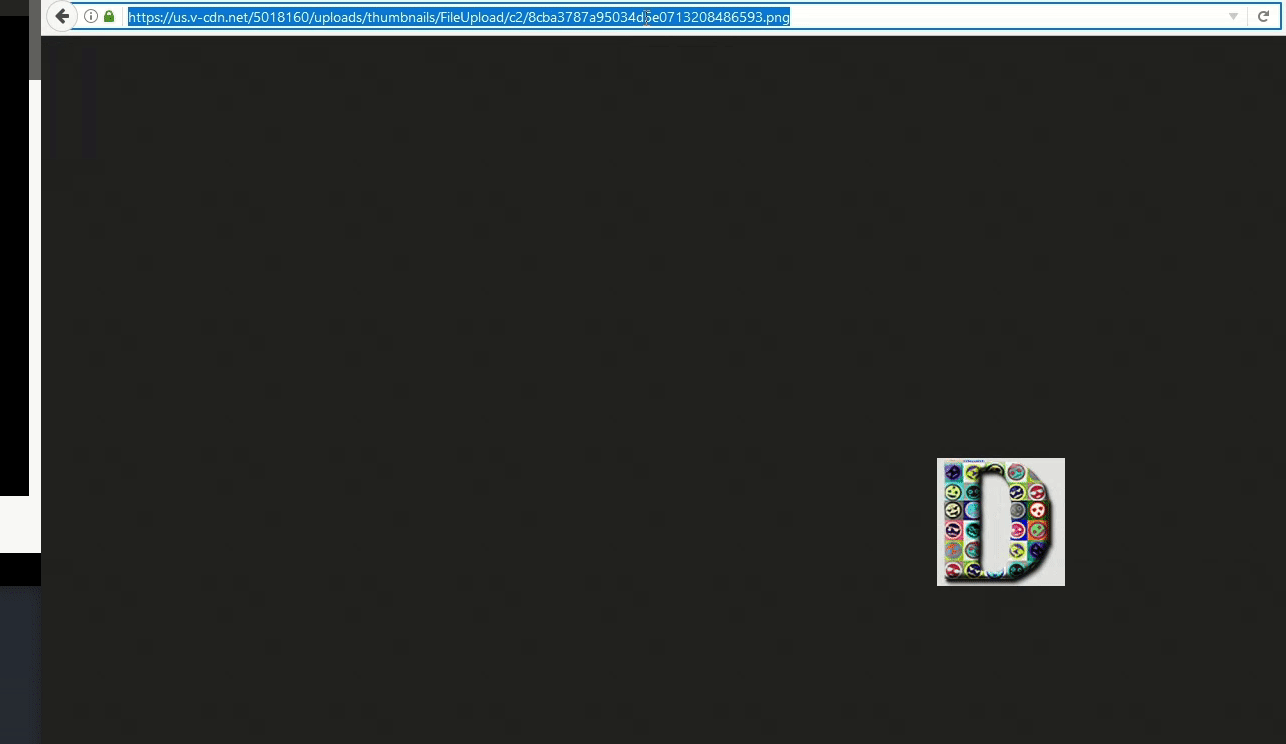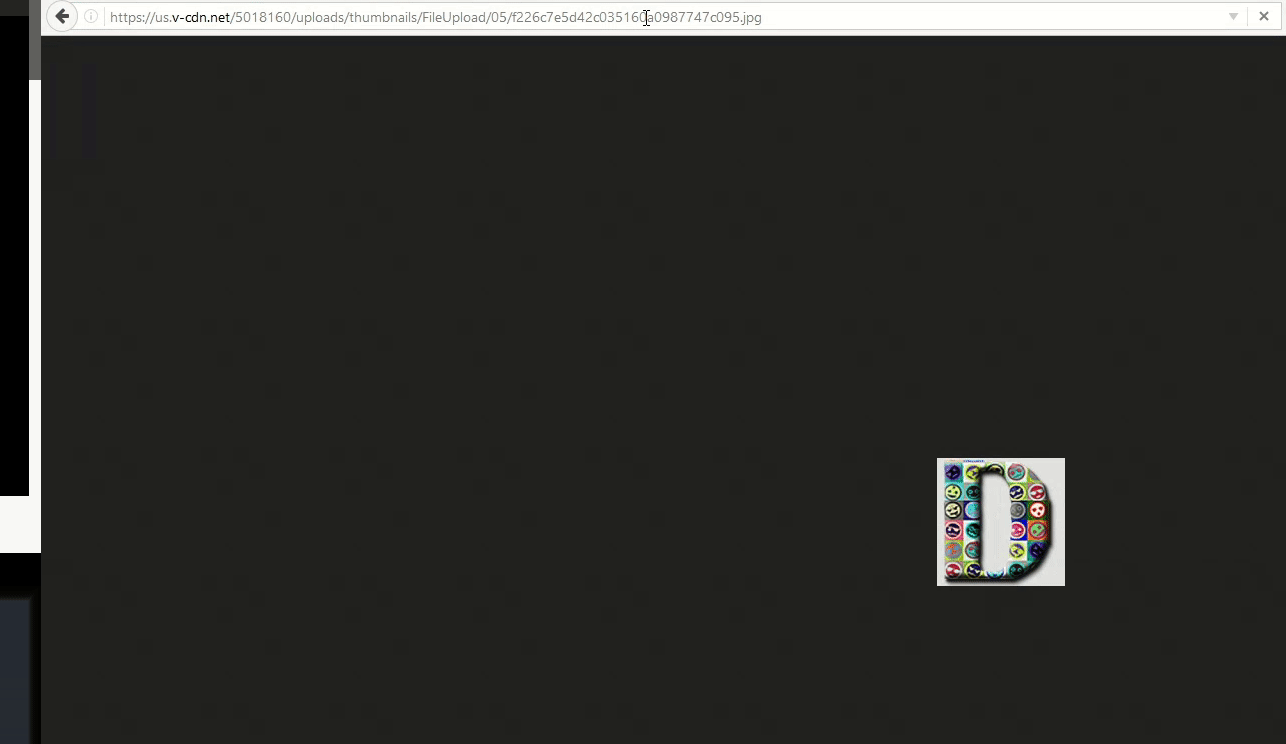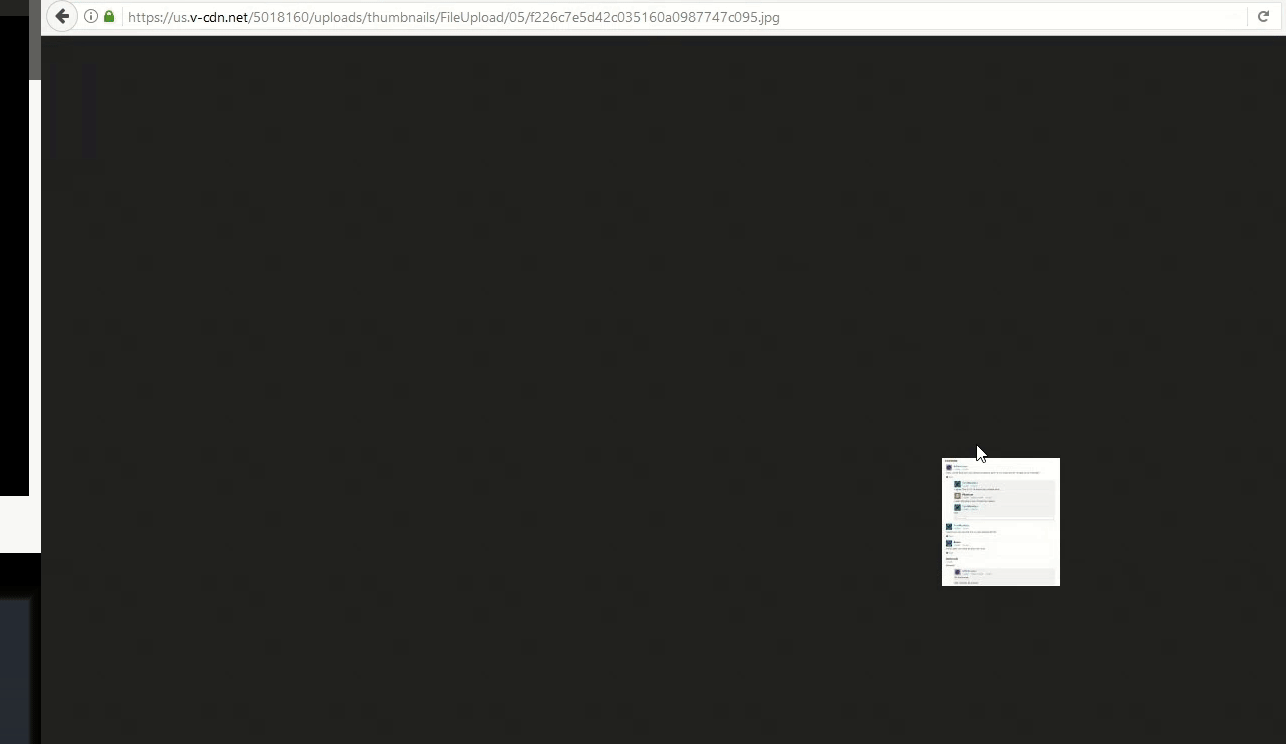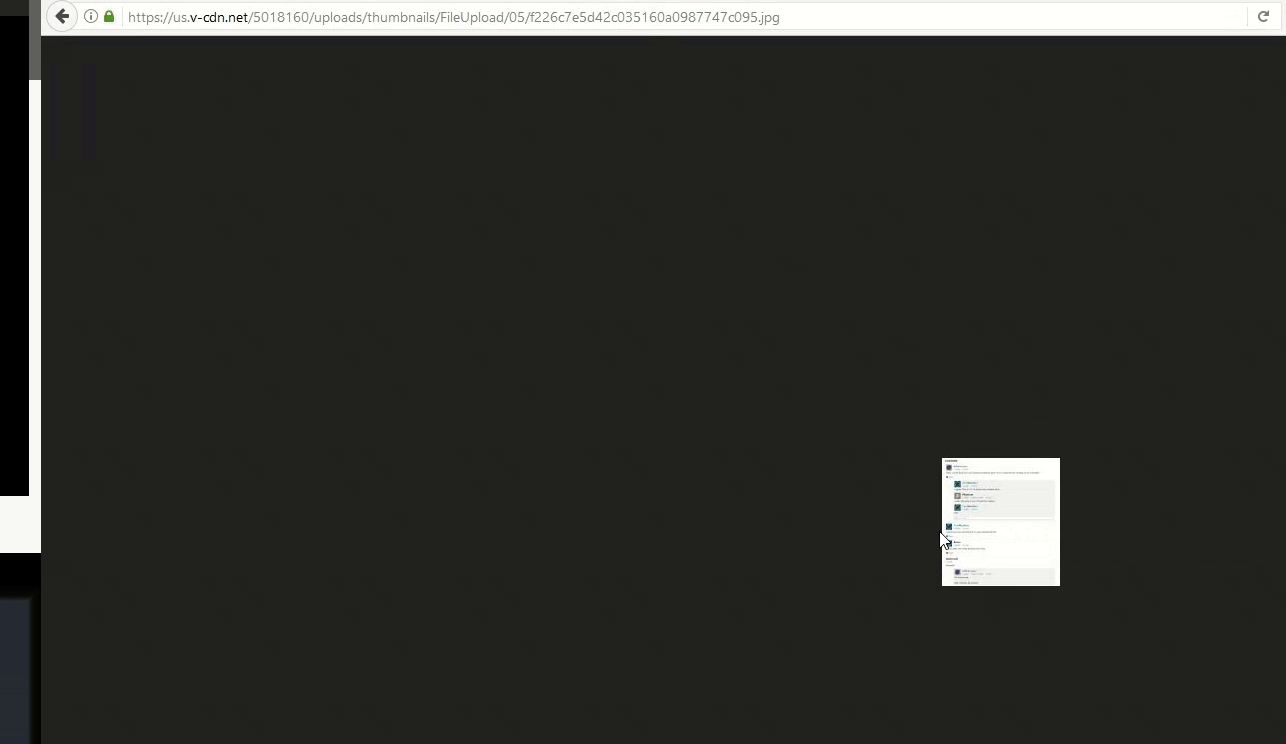
Images are commonly vulnerable to this kind of vulnerability, as seen in report 258260:
Some alternate sites of the main one may contain vulnerabilities which were patched in the main one. Try different regional top level domains, or APIs on different
![]()
IDOR is probably the easiest way to get a high priority account takeover. However, tunnel vision-ing this objective can stop you from spotting IDORs which results in different, or lower priority IDORs. Instead, think about:
Does it leak PII (293490, 980511, 723461, 668439, 783708, 439729, 152407)293490 Shows us how an IDOR can result in leaking emails of all users in a response. Leaking PII.



If you thought any of this information was useful, following would be a free and easy way to support me, my goal is to reach 100 followers, and we’re already 60% of the way there! I look forward to posting more informational content.
PS I see when people tweet my articles and I always really appreciate it. 💙
*DISCLAIMER: I take no responsibility for any actions committed by readers. Only perform enumeration on targets you have permission for. Always read and check the scope of a program for guidance. These reports were scraped and read on 10th of March 2021, and some of them were not fully disclosed or in different langauges.
.png)
 2 years ago
140
2 years ago
140 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·