BOOK THIS SPACE FOR AD
ARTICLE ADReading some topics at the Internet, it became clear that I'm not alone who have wondered why Google Chrome web browser (on Windows) runs so many processes even if one or two tabs have been opened in the browser. This situation looks more strange when I just have opened tabs without any content. In this blog post I want to talk about some hidden features of Chrome, which can be a cause of such behavior. The purpose of a blog post is obvious - try to understand and explain nature of Chrome's processes. As I got no feedback from Chrome evangelists, I have tried to get answers to these questions independently.
As everyone already knew, Chrome web browser is based on a multi-process architecture. This means that it creates more than one process during its work for various purposes. Among others, major advantage of such concept is opening each tab in a separate process that leads to minimizing possible data loss or other tabs crash, when a single web page doesn't respond. In such scenario, you can terminate one non-responsive tab without harming others. Another obvious reason of MP architecture is famous Chrome's sandbox.
Let's look at a simple experiment. We can take a clean Chrome installation and check these strange things with much running processes.
It is clean 64-bit release of Chrome installation, where special experimental features like AppContainer, Strict site isolation and others are turned off. In web browser only a blank web page is opened. WS Private indicator is a counter of physical memory that was committed by the browser. Another indicator, Private Bytes, represents amount of virtual memory was committed by Chrome's processes, but along with resident physical memory, it also includes committed virtual memory that is residing at page file (non resident, swapped out, but committed). Thus, next types of processes Chrome runs as you started it ("from-the-box", clean installation of the 64bit release browser's version at Win10 with default settings).
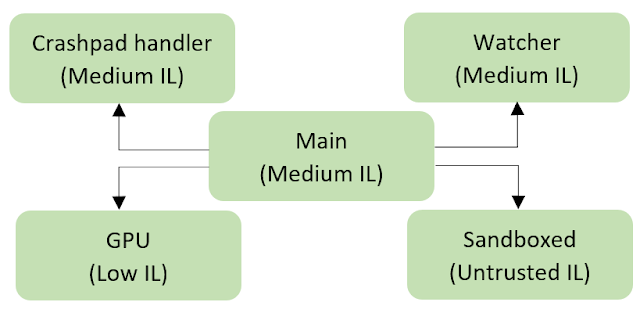
As you can see from the scheme above, each process is intended for a specific purpose. The Crashpad handler process is so-called a crash-reporting system (link) as Google calls it. From technical info following this link, we can understand that the Crashpad handler helps to the web browser report some sort of info and, probably, crash dumps to Google servers. As they write.
"Crashpad is a library for capturing, storing and transmitting postmortem crash reports from a client to an upstream collection server. Crashpad aims to make it possible for clients to capture process state at the time of crash with the best possible fidelity and coverage, with the minimum of fuss.
Crashpad also provides a facility for clients to capture dumps of process state on-demand for diagnostic purposes."
The Watcher process, as meaning by its name, is serving for to track Chrome's processes state and check whether it hanged.
Chrome leverages GPU to perform (accelerate) drawing some sort of graphics, including, CSS, graphical elements and usual web-page rendering. This process is called GPU process. This feature is turned on by default. And, seems, can't be turned off, even with resetting this option at the browser's options.
Can't be turned off, because, from my experience, even when I disabled this feature, the browser still was instructed to use GPU. Probably, with turning off this feature, the browser haven't to create additional processes for this purpose.
Interesting thing that the GPU process also can be sandboxed with Windows 8+ security feature called AppContainer.
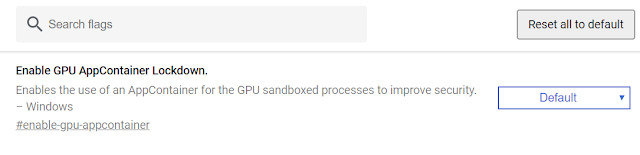
Chrome also contains some security features that theoretically can contribute of creating more processes. For example, the browser has a special security feature that is used for Spectre #1 security vulnerability (link) mitigation. It is called "Strict site isolation".
As you can see from the scheme above, each process is intended for a specific purpose. The Crashpad handler process is so-called a crash-reporting system (link) as Google calls it. From technical info following this link, we can understand that the Crashpad handler helps to the web browser report some sort of info and, probably, crash dumps to Google servers. As they write.
"Crashpad is a library for capturing, storing and transmitting postmortem crash reports from a client to an upstream collection server. Crashpad aims to make it possible for clients to capture process state at the time of crash with the best possible fidelity and coverage, with the minimum of fuss.
Crashpad also provides a facility for clients to capture dumps of process state on-demand for diagnostic purposes."
The Watcher process, as meaning by its name, is serving for to track Chrome's processes state and check whether it hanged.
Chrome leverages GPU to perform (accelerate) drawing some sort of graphics, including, CSS, graphical elements and usual web-page rendering. This process is called GPU process. This feature is turned on by default. And, seems, can't be turned off, even with resetting this option at the browser's options.

Can't be turned off, because, from my experience, even when I disabled this feature, the browser still was instructed to use GPU. Probably, with turning off this feature, the browser haven't to create additional processes for this purpose.
Interesting thing that the GPU process also can be sandboxed with Windows 8+ security feature called AppContainer.

Chrome also contains some security features that theoretically can contribute of creating more processes. For example, the browser has a special security feature that is used for Spectre #1 security vulnerability (link) mitigation. It is called "Strict site isolation".
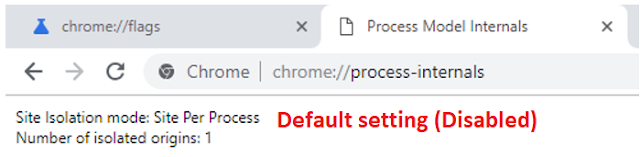
Yes, with activated feature, each site user opens will be isolated into a separate process. For Spectre #1 this mitigation is useful, because exploiting speculative execution flaws with help of scripting languages, an attacker may steal sensitive user's data that is intended for another site, for example, online banking. Thus, a malicious script from crafted page can get access to trusted site's data that is played in the same browser's process. If Chrome isolates each site in separate process, this situation becomes impossible. But obvious side effect in such scheme is more working Chrome processes into a system.
But if you look at description of this feature, you will be surprised that it turned on by default even if it marked as not working (disabled actually means default behaviour). Probably Chrome's managers have decided to protect users from speculative execution side-channel flaws by default. Thus, it's one more reason why you see a lot of running processes of the browser.
But if you look at description of this feature, you will be surprised that it turned on by default even if it marked as not working (disabled actually means default behaviour). Probably Chrome's managers have decided to protect users from speculative execution side-channel flaws by default. Thus, it's one more reason why you see a lot of running processes of the browser.
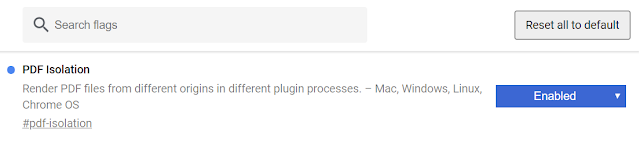
Chrome also can play PDF content in a separate plugin process (default setting). That also implies creating of additional processes for each opened document. PDF isolation inside a separate process is important, because major part of all RCE exploits are being targeted to Adobe Reader of Flash plugins.
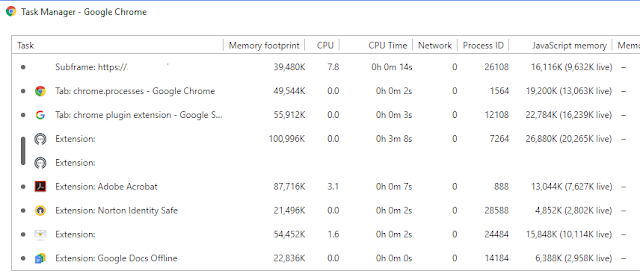
Also, according to Chrome's task manager, it can create processes for the web-page frames and browser's extensions (plugins), applications. Processes for various content you can find on the screenshot below.
I've also been testing Google Chrome on Windows 10 to understand what security features it supports. The browser has been shown very good results (Windows 10 RS4).
.png)


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·