Modify version of impacket wmiexec.py,wmipersist.py. Got output(data,response) from registry, don't need SMB connection, but I'm in the bad code :(
Specially Thanks to:
@rootclay, wechat: _xiangshan
Overview
In original wmiexec.py, it get response from smb connection (port 445,139). Unfortunately, some antivirus software are monitoring these ports as high risk.
In this case, I drop smb connection function and use others method to execute command.
BTW, win32_scheduledjob has been disabled by default after windows NT6. Here is the way how to enable it.
wmipersist-wip.py (Highly recommend, !!!only works on impacket v0.9.24!!!): A Python version of WMIHACKER, which I picked the vbs template from it. Attacker can use it to do lateral movement safety under antivirus-software running.
wmiexec-regOut.py: Just a simple Win32_Process.create method example .
How it works?
wmiexec-wip.py workflow:
Step 1:
WMIC authenticated remotlyStep 2:
Use win32process class and call create method to execute command. Then, write down the result into C:\windows\temp directory named [uuid].txtStep 3:
Encode the file content to base64 strings (need to wait a few seconds)Step 4:
Add the converted base64 string into registry, and key name call [uuid]Step 5:
Get the base64 strings remotly and decode it locally.wmipersist-wip.py workflow:
Step 1:
Add custom vbs script into ActiveScriptEventConsumer class.Step 2:
Creating an Event Filter.Step 3:
Trigger FilterToConsumerBinding class to PWNED!Requirements
Generally, you just need to install official impacket.
PortalUsage
wmiexec-wip.py usage:
With cleartext password
Name: EnableAt
Type: REG_DWORD
Value: 1
With NTLM hashes
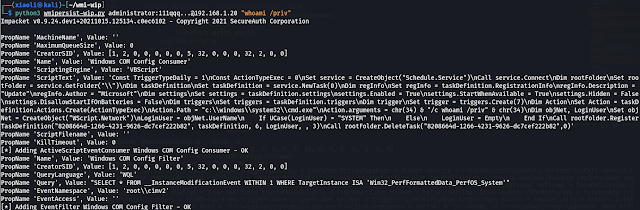
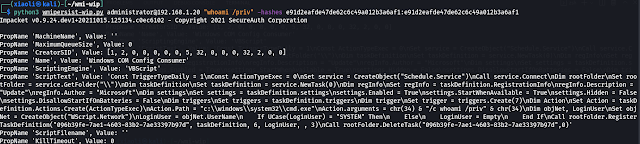
wmipersist-wip.py usage (Default is no output):
With cleartext password (without output)
With NTLM hashes
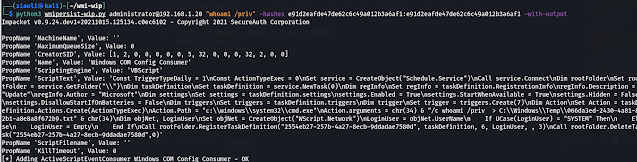
With output
Under Huorong antivirus-software (Using WMIHACKER VBS template!!!) 
Cheatsheet
Do not forget to clean up temp directory after run command with out put.
Command: del /q /f /s C:\windows\temp\*

Command include double quotes.
Make double quotes inside single quotes wevtutil cl '"security"'

.png)
 2 years ago
137
2 years ago
137 


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·