BOOK THIS SPACE FOR AD
ARTICLE AD
The Flubot malware has switched to a new and likely more effective lure to compromise Android devices, now trying to trick its victims into infecting themselves with the help of fake security updates warning them of Flubot infections.
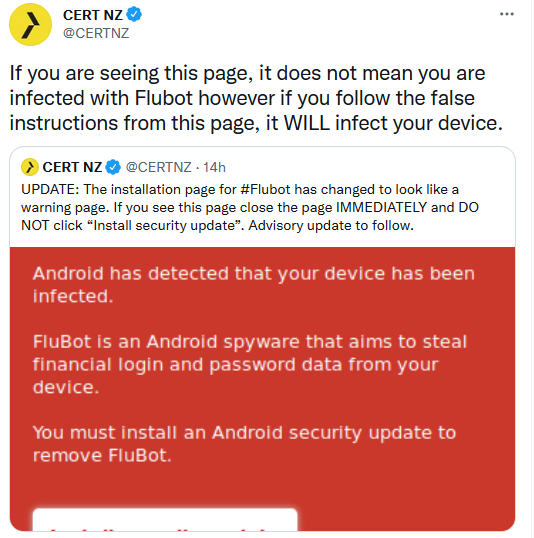
As New Zealand's computer emergency response team (CERT NZ) warned earlier today, the message on Flubot's new installation page is only a lure designed to instill a sense of urgency and pushing potential targets to install malicious apps.
"Your device is infected with the FluBot® malware. Android has detected that your device has been infected," the new Flubot installation page says.
"FluBot is an Android spyware that aims to steal financial login and password data from your device. You must install an Android security update to remove FluBot."
Potential victims are also instructed to enable the installation of unknown apps if they're warned that the malicious app cannot be installed on their device.
"If you are seeing this page, it does not mean you are infected with Flubot however if you follow the false instructions from this page, it WILL infect your device," CERT NZ explained.
The SMS messages used to redirect targets to this installation page are about pending or missed parcel deliveries or stolen photos uploaded online.
This banking malware (also known as Cabassous and Fedex Banker) has been active since late 2020, and has been used to steal banking credentials, payment information, text messages, and contacts from compromised devices.
Until now, Flubot spread to other Android phones by spamming text messages to contacts stolen from already infected devices and instructing the targets to install malware-ridden apps in the form of APKs delivered via attacker-controlled servers.
Once deployed via SMS and phishing, the malware will try to trick the victims into giving additional permissions on the phone and grant access to the Android Accessibility service, which allows it to hide and execute malicious tasks in the background.
Flubot will effectively take over the infected device, gaining access to the victims' payment and banking info in the process via downloaded webview phishing page overlayed on top of legitimate mobile banking and cryptocurrency apps' interfaces.
It also harvests and exfiltrates the address book to its command-and-control server (with the contacts later sent to other Flubot spam bots), monitors system notifications for app activity, reads SMS messages, and makes phone calls.
The botnet has mainly targeted Android users from Spain at the beginning. Still, it has expanded to target additional European countries (Germany, Poland, Hungary, UK, Switzerland) and Australia and Japan in recent months, even though the Catalan police reportedly arrested the gang's leaders in March.
Since Swiss security outfit PRODAFT said in March that the botnet was controlling roughly 60,000 devices that collected the phone numbers of 25% of all Spanish citizens, the malware will likely spread even quicker now that it uses what looks like even more effective lure.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·