BOOK THIS SPACE FOR AD
ARTICLE AD
The Hydra banking trojan is back to targeting European e-banking platform users, and more specifically, customers of Commerzbank, Germany’s second-largest financial institution.
MalwareHunterTeam has spotted the two-year-old malware in a new distribution campaign that targets German users with a malicious APK named 'Commerzbank Security' and using the same icon as the official app.
This sparked the interest of Cyble researchers, who sampled the file for a more in-depth analysis which revealed a powerful phishing tool with extensive access to permissions.
"Commerzbank.apk": 5e9f31ecca447ff0fa9ea0d1245c938dcd4191b6944f161e35a0d27aa41b102f
From: http://kunden.Commerzbank.de-id187dbbv671vvdazuv1zev789bvdv681gfbvazvuz8178g4[.]xyz/dl/coba/index.php - resolving to 91.214.124[.]225, there are more domains like this resolving there... pic.twitter.com/StSv2Dijlc
A galore of permissions
Cyble has found that the Hydra-laced app requests 21 permissions, most notably the 'BIND-ACCESSIBILITY_PERMISSION' and 'BIND_DEVICE_ADMIN,' two extremely risky permissions. The former ensures that the app is always running in the background, monitoring and intercepting all data that comes and goes to and from the device. The latter is practically giving the trojan admin privileges on the device, so a wide range of exploitation possibilities opens up.
Other risky permissions used by the trojan include:
| Permission Name | Description |
| CHANGE_WIFI_STATE | Modify Device’s Wi-Fi settings |
| READ_CONTACTS | Access to phone contacts |
| READ_EXTERNAL_STORAGE | Access device external storage |
| WRITE_EXTERNAL_STORAGE | Modify device external storage |
| READ_PHONE_STATE | Access phone state and information |
| CALL_PHONE | Perform call without user intervention |
| READ_SMS | Access user’s SMSs stored in the device |
| REQUEST_INSTALL_PACKAGES | Install applications without user interaction |
| SEND_SMS | Allows the app to send SMS messages |
| SYSTEM_ALERT_WINDOW | Allows the display of system alerts over other apps |
These permissions can be abused to access SMS content, send SMSs, display system alerts, modify device settings, perform calls, write and read external storage, modify WiFi settings, install additional apps, and more.
None of these activities requires interaction by the victimized user, so once the malware has infected the device, it’s already too late.
New features and enhancements appear
The fake Commerzbank app sends bulk SMS to the victim’s contact list, creates overlays on other apps, screencasts the device screen back to the actor’s system, hides its icon, and steals OTPs (one-time passwords) as well as the screen lock PIN.
A notable new feature is the incorporation of TeamViewer relying on the abuse of the Accessibility service, which has not been documented in previous Hydra variants.
New enhancements that aim to make the detection of the trojan harder include the use of encrypted TOR communications, enabling SOCKS Proxy for redirection, and disabling Play Protect, Android’s default security component.
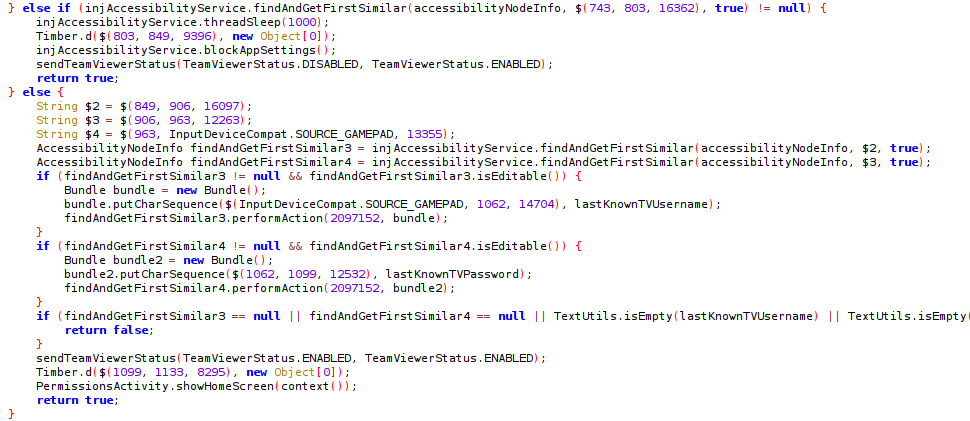 Enabling TeamViewer through the Accessibility service.
Enabling TeamViewer through the Accessibility service. Source: Cyble
A large pool of targets
Commerzbank serves 13 million customers in Germany and another 5 million people in Central and Eastern Europe. This makes up for a total of 18 million potential targets, which is always a critical consideration for malware distributors.
Typically, the threat actors use SMS, social media, and forum posts to lure their prospective victims to malicious landing pages that drop the APK onto German smartphones.
If you think you may have fallen in Hydra’s trap already, it is recommended that you clean your device with a security tool from a reputable vendor and even perform a factory reset afterwards.
In general, you should only install APKs from trustworthy sources (the bank’s website or Google Play), activate 2FA on your online banking account, and keep your device’s OS and AV up to date.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·